Challenge
For this challenge, you are given a 16gb disk .img (disk image file). Normally when your given a disk image, you are probably trying to discover (or recover), some sort of information that was stored on the disk.
TL;DR
You are given a disk image which ends up being from a raspberry pi. Mount the raspberry pi image by reading this page or using some forensic utility like Autopsy. Explore the file system a bit until you discover the login credentials for the web application located at /var/www/ there you’ll find a username (admin) and password (iforgotaboutthemathtest) in some text files, submit the creds and get the flag.
Long(er) Explaination
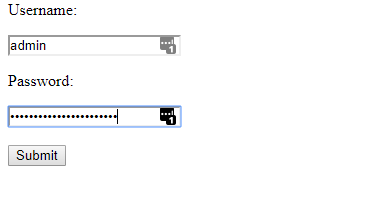
Looking at the challenge site http://forensics.chal.csaw.io:3287 you are presented with a login page. So likely we are going to have to extract a username and password from the best_router image.
My favorite utility to use for tasks like this is Autopsy. Autopsy is a powerful forensics tool, which allows you to analyze disk images, as well as some other additional neat addons.
Extracting the Image
We are going to go ahead in un-tar the archive, the final disk image ends up being around 16Gb.
Medic@dastiniaa:/mnt/y/ctf/csaw/best-router$ tar -xvf true.tar
tar: Ignoring unknown extended header keyword 'LIBARCHIVE.creationtime'
tar: Ignoring unknown extended header keyword 'SCHILY.dev'
tar: Ignoring unknown extended header keyword 'SCHILY.ino'
tar: Ignoring unknown extended header keyword 'SCHILY.nlink'
best_router.img
Exploring the Best Router Image
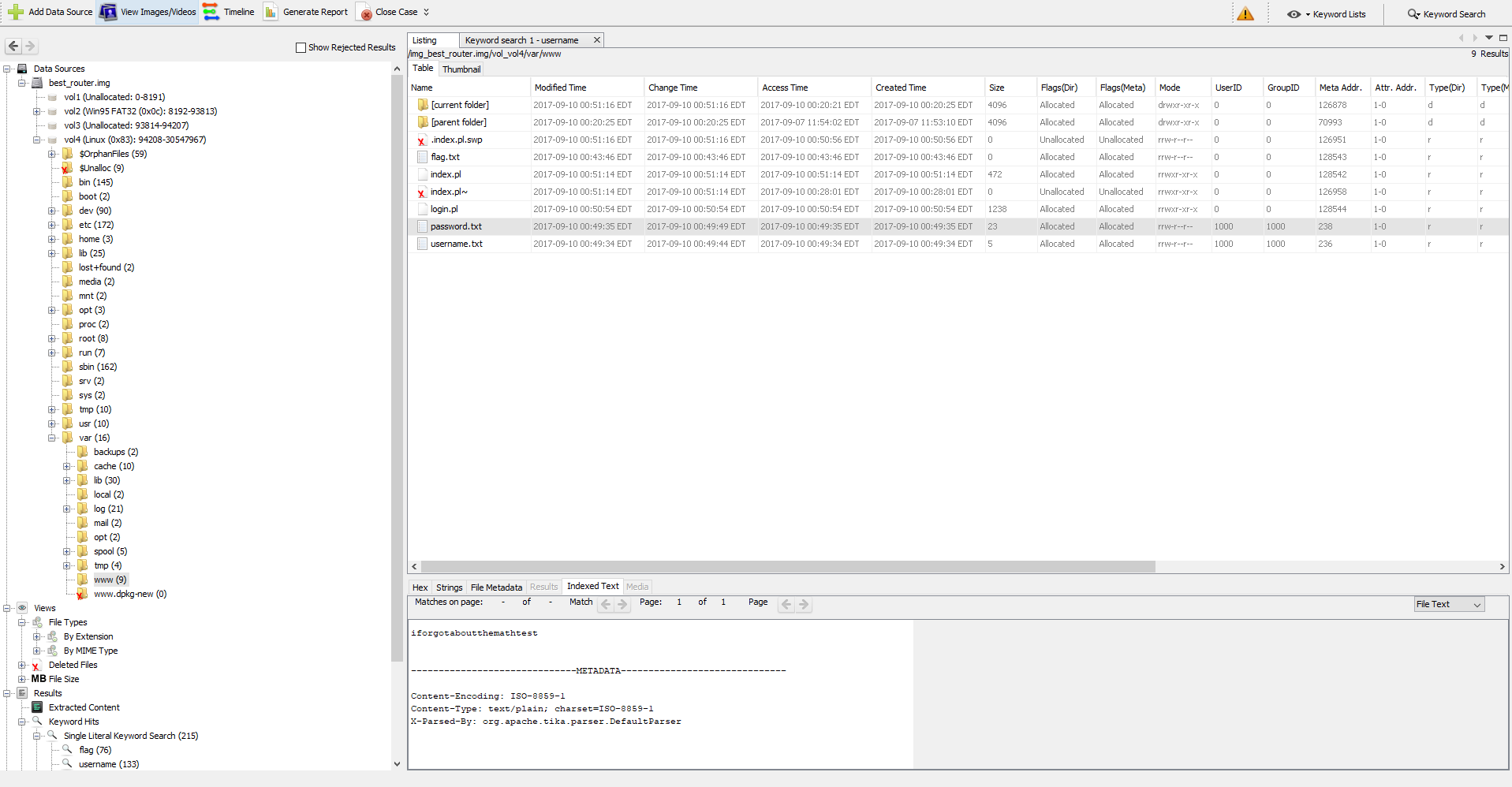
After creating a new case within Autopsy, and adding the best_router.img as a data source. Autopsy will start indexing and categorizing the files in the file system into groups. You can do a keyword search for flag, username or password and autopsy will group the keyword hits into a view.
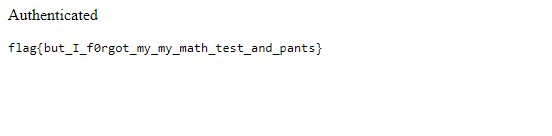
You’ll discover a few text files, conveniently named username.txt, password.txt, flag.txt (empty). Get the username and password from these files and submit them inside the web app, and you get the flag.

Overall this was a pretty simple challenge.